Last Update : 03/01/2023
Quick Principles Check List
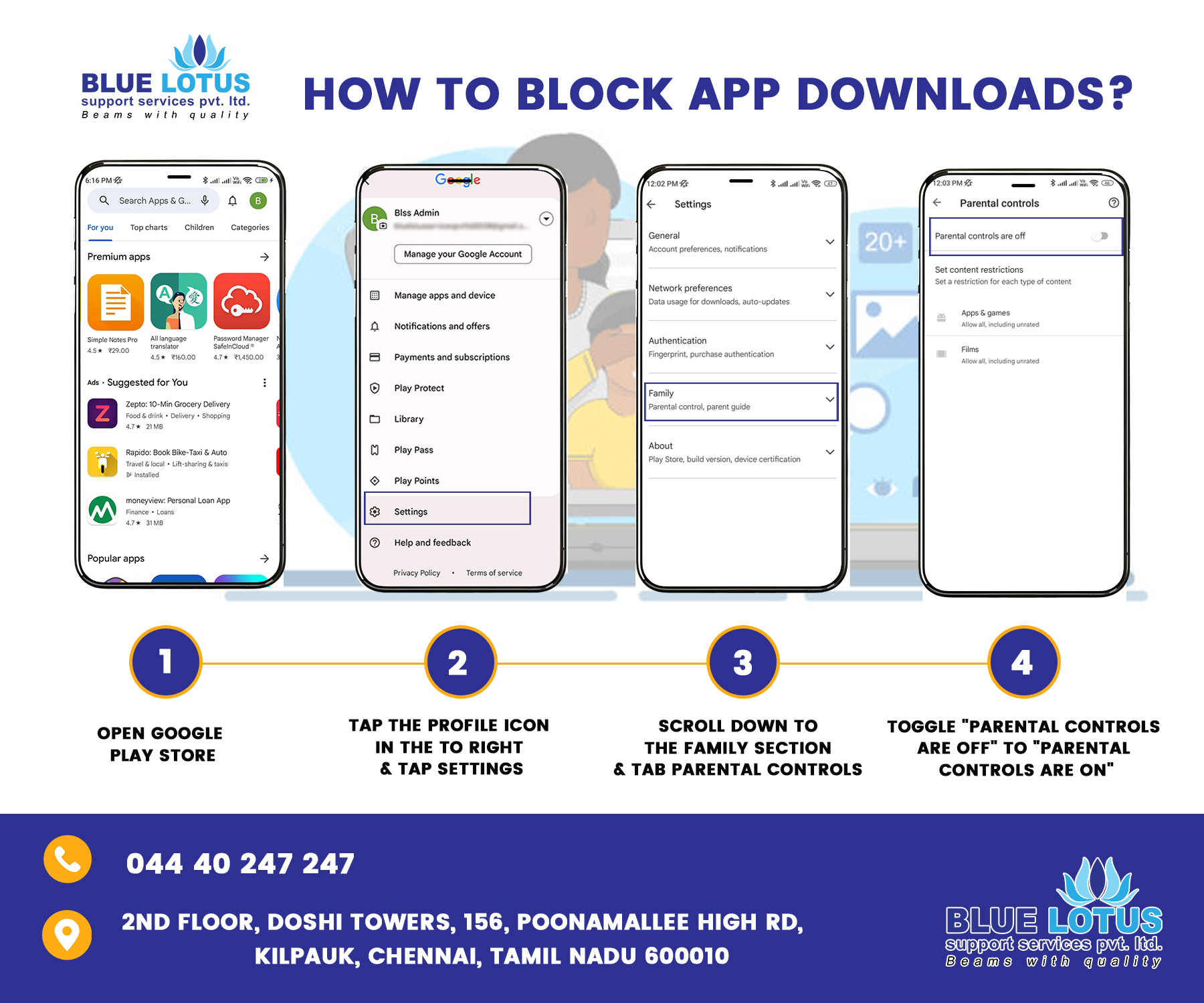
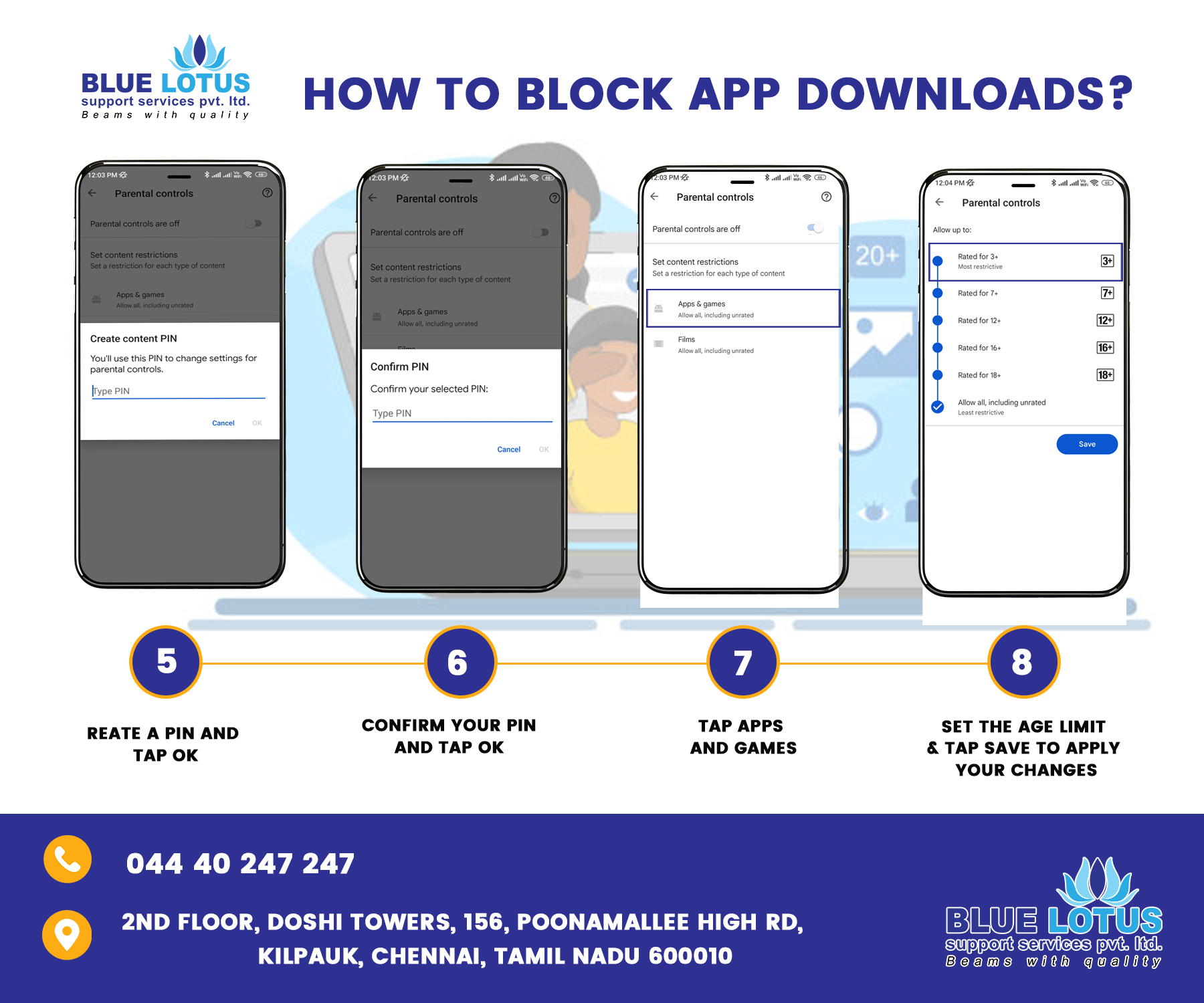
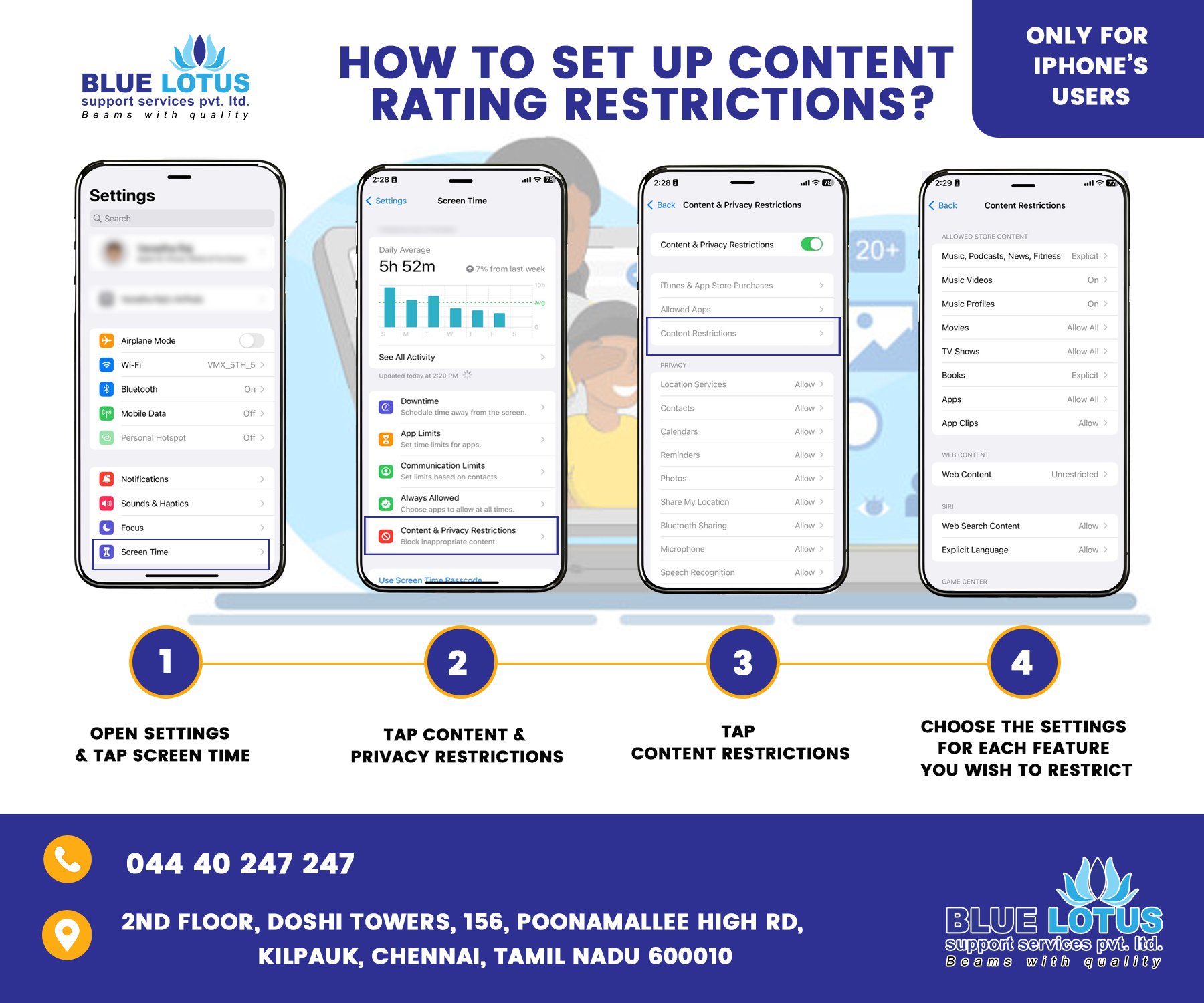
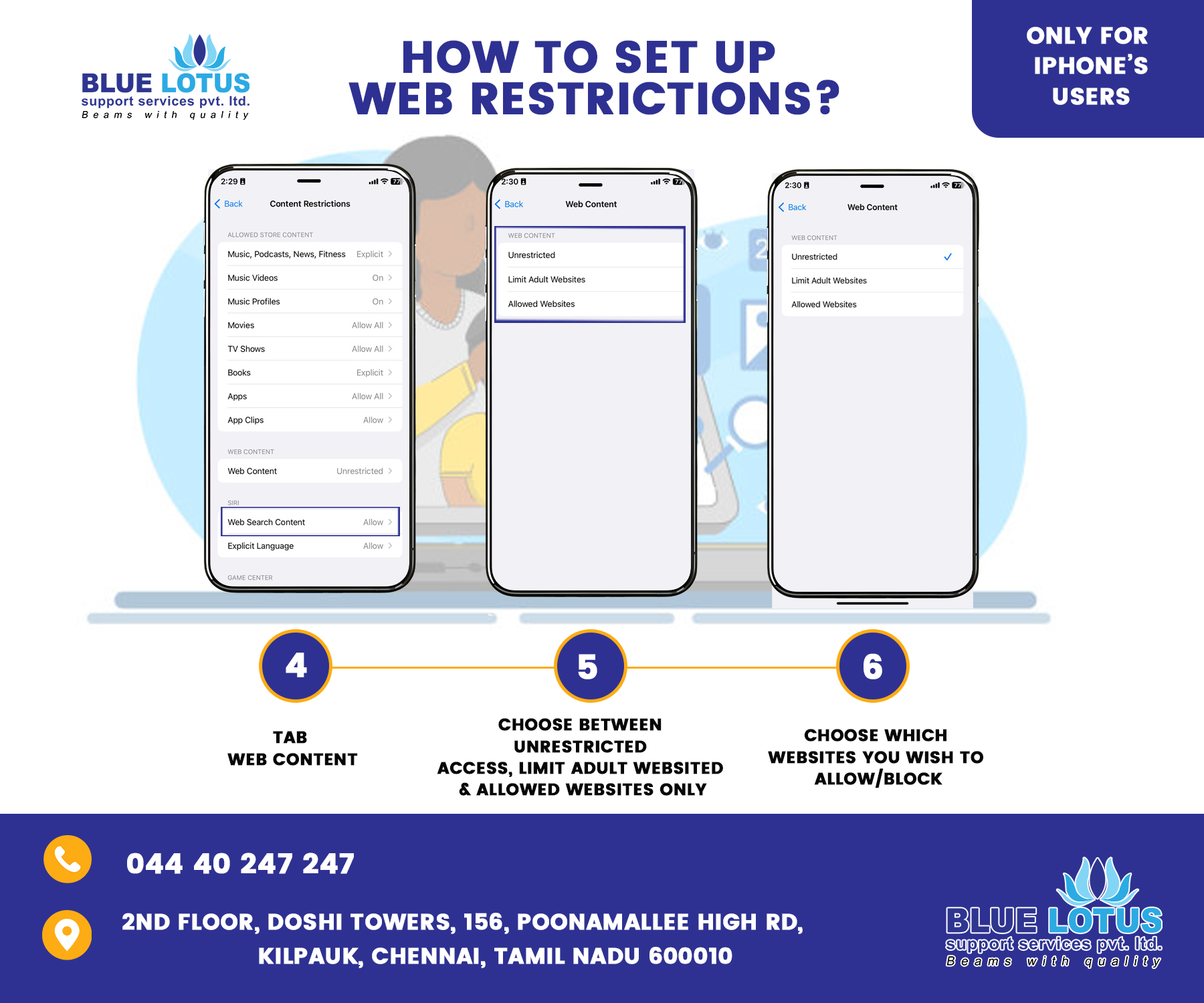
Internet to be used safely for children
The technology agenda for kith and kin as well as teens are far from straightforward. Not every kith and kin teenager uses the same technology. Factors such as the child’s maturity level, parent’s view; and approach to devices at home, school and friend’s houses come into play With these mind, we are explaining a Principles checklist for parents of children at any age, which are highlights the actions you should take care of your entire family. These are by no means precise lists (the tech world moves far too quickly to be able to promise that!) but they are used to starting point. We hope you find them useful. For more details, please visit....
Energetic principles Lists
• Considering about how you guide your family in the real world and do the same in the digital world. Don’t be afraid to set boundaries and rules for your child from a young age. • We have to generate the most of tools like Parental Controls on computers, mobiles and games consoles; privacy features on social networking sites; and safety options on Google and other search engines. • We have to go some of the technology your son or daughter enjoys. Play on them together or ask them to help set you up on Face book if you’re not already a member. • We have to try not to use technology as a babysitter too often. We all do it sometimes but it’s important to know what your child is doing. • We are composing digital issues part of everyday conversation. Show your child that you understand how important technology is to them and talk about all its amazing benefits, but don’t shy away from difficult subjects like responsible online behaviour, bullying and pornography. • We need to set specific internet guidelines for your children to live by and consistently enforce consequences if they are not being followed. Manage your children’s time on the internet. • Figured out Internet Privacy Policies as they apply to your child. Parents should be aware of these for protecting their children’s privacy on the web. Find out more here: http://www.ftc.gov/privacy/privacyinitiatives/childrens.html • Conceive strong passwords for different websites using a good mix of alphabets, numbers and special characters and make sure that you do not disclose your passwords to anyone (except your parents). • Don’t affirm personal information like name, address, date of birth, school details, passport number, credit card numbers, telephone numbers or family members’ names, or location details/whereabouts on social websites (especially when you are alone at home). • Don’t be friend or strangers. To assure that your group involves only people known to you in person (such as friends and family). If someone approaches you, ensure that you are escorted with a responsible elder/parent and meet only in public places where many people are around. • To decrease the viewership of your social account/site to only those who are well known to you. Always use security and privacy settings of websites to access and manage your profile information from time to time. • If anyone bothers you or is unfriendly, use ‘block’ or ‘unfriendly’ tools available on social sites. Should you receive any strange/unfriendly/abusive request or communication, immediately bring it to the notice of parents/elders in the family. • We have to Keep police and emergency numbers saved in your mobile contacts. • Don’t over-share pictures of home, yourself or your family on the internet. Never share your personal pictures or information without first checking with your parents/responsible elder. • Pay specific attention to the language you use online and think before you post your pictures or videos or updates. Avoid posting information when you are angry or emotionally disturbed. • Make sure that you log in or sign in and log out or sign out of your accounts. • Ensure before downloading or installing any app or software on your computer/mobile phone, it is good to first check with your parents or responsible elder to avoid damage to your device or jeopardize privacy. • Don’t say or do anything that would hurt other people’s feelings or, that is against the law and puts you in bad light. • Reveal your correct age when signing up on websites to ensure safe use of the internet. Visit only those websites that are relevant for your age. If you inadvertently click any website that displays adult content or any offensive/abusive content, close such websites immediately and keep your parents/responsible elder informed. • Make sure that your computer/tablet/mobile phone has up-to-date security software as well as parental control software installed for safe internet use. • Fix scheduled timings with your parents to access social sites and adhere to them. Meet your friends in person and play with them outdoors. • Be aware of certain activities that are treated as cybercrimes by law: o Cyber angling – where someone is repeatedly and persistently followed and pursued online by email or other electronic means. o Cyber imperious – where someone harasses, embarrasses, taunts, insults or uses threatening behaviour by using internet, email or other electronic means. o Child smut – where someone captures/displays/sends images or videos of child/children (below 18 years) in an obscene or indecent (i.e. sexually explicit) manner. o Pornography – where someone captures/displays/sends images or videos of the private body parts of any person without his/her consent. o Hacking – where someone accesses or uses the computer/laptop/mobile or email or social sites’ accounts of another person without authorization/consent of that person (such as Gmail, Facebook, Twitter and other such social networking sites). This includes destroying or deleting or altering any information residing on such devices/websites. o Identity and analyze theft – where someone uses the password or any other unique identification feature of another person without authorization or consent of that person. o Cyber terrorism – where someone attempts to gain access to a computer or laptop or mobile without authorization or consent or causes denial of access to that person who is authorized to access that computer or laptop or mobile. o Offensive communication – where someone sends any grossly offensive information of another person which is known to be false for the purpose of annoying, inconveniencing, insulting, deceiving, or taking vengeance.



 NEW BMS
NEW BMS